Wrench Attack
Privacy in Cryptocurrency: How to Avoid the Wrench Attack Economy
Introduction: The Problem with Public Blockchains
In the modern world, privacy isn’t just a luxury—it’s a necessity. But in crypto, privacy is often an afterthought. People praise decentralization, censorship resistance, and financial sovereignty, but conveniently forget that all their transactions are visible on a public ledger, forever...
If you tap to pay on base, whatever activity you're doing will be immutably visible to the entire world forever, and whoever is receiving your payment can view your entire financial state at any moment in time and all your activity in the past and future
Imagine walking around with your entire bank statement tattooed on your forehead. That’s basically what using a public blockchain like Bitcoin or Ethereum looks like today. The moment you send someone a payment, they can:
- See your entire transaction history
- Track every future transaction you make
- Estimate your net worth with some basic blockchain forensics
Now, combine this with the fact that physical violence is still a very effective and low-tech way to separate people from their money—and you’ve got a real problem. Welcome to the "wrench attack economy."
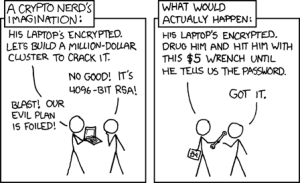
What Is a Wrench Attack?
A wrench attack (also known as a $5 wrench attack) is when someone skips the hacking, exploits, and fancy cryptography—and just threatens you with a literal wrench (or any other blunt object) until you hand over your private keys.
No need for a 0-day exploit. No need to crack encryption. Just good old-fashioned violence and intimidation.
Now, imagine this scenario:
- You own a corner store and accept USDC payments
- Some guy walks in and buys a bottle of soda for $2
- You check his wallet address and see he’s sitting on 200 ETH ($700,000+)
- You blink at your security guard twice—the secret signal for "wrench attack time"
See the problem? Public blockchains turn everyone into an intelligence agency. Criminals no longer have to guess who’s worth robbing. The blockchain tells them directly.
The False Promise of Pseudonymity
Some crypto enthusiasts argue that wallet addresses aren’t tied to real identities, so it’s fine. Wrong.
The moment you:
✔️ Withdraw from an exchange with KYC
✔️ Use your wallet address for a purchase
✔️ Receive funds from an identifiable source
Your pseudonymity is gone. Services like Chainalysis, Elliptic, and Nansen can easily track your movements, and your entire financial history becomes an open book.
It gets even worse when governments start issuing on-chain IDs (think CBDCs or Ethereum’s ENS names tied to real-world identities). Once that happens, privacy isn’t just dead—it’s immutably dead.
How Privacy Coins and Techniques Can Help
The good news? Crypto privacy is possible. But it requires using the right tools.
1. Privacy Coins (Monero, Zcash, Firo)
- Monero (XMR): Uses Ring Signatures, Stealth Addresses, and Confidential Transactions to hide amounts, sender, and receiver.
- Zcash (ZEC): Uses zk-SNARKs to allow fully private transactions (if shielded).
- Firo (FIRO): Uses Lelantus to allow trustless, untraceable transactions.
Unlike Bitcoin or Ethereum, where transactions are visible forever, these privacy coins obfuscate financial history, making it impossible for attackers to figure out how much you have or where it’s going.
2. CoinJoins & Mixing Services (for Bitcoin & Ethereum)
If you’re stuck using BTC or ETH, you can still increase privacy with:
- Wasabi Wallet & Samourai Whirlpool (Bitcoin CoinJoins)
- Tornado Cash (Ethereum) (RIP, banned but still functional)
- Aztec Network (Ethereum private transactions)
These tools break the link between sender and receiver so people can’t just look up your wallet and say, "Ah yes, this guy is loaded."
3. Stealth Addresses & Payment Codes
Instead of using a single, reusable address (which links all your transactions), use:
- Stealth Addresses (Monero, Ethereum stealth tech)
- PayNyms (Bitcoin BIP47 Payment Codes)
These generate a unique, one-time address for each transaction, so even if someone pays you regularly, they can’t see your total balance or past transactions.
4. Off-Chain Transactions (Lightning Network, Cash App, etc.)
For small purchases, consider off-chain methods:
✔️ Lightning Network (BTC) – Fast & private payments (to an extent)
✔️ Cash App, Venmo, PayPal (fiat but off-chain) – No blockchain history
✔️ Local Monero/Zcash OTC deals – Avoid blockchain linking
Keeping small transactions off-chain prevents you from doxxing your entire financial history just because you wanted to buy a coffee.
The Future: Can Privacy & Crypto Coexist?
Governments and blockchain surveillance companies hate privacy because it makes tracking users difficult. They push for regulated, KYC-only chains, hoping to make crypto as trackable as the banking system.
But let’s be real:
- Privacy is a fundamental right.
- Nobody wants their net worth broadcast to every merchant they interact with.
- Wrench attacks become far less viable when attackers have no idea who’s rich.
For crypto to be usable in the real world, privacy tools must become default, not optional. Otherwise, the dream of financial sovereignty turns into a dystopian nightmare where every transaction is permanently tracked, taxed, and monitored.
Conclusion: Stay Private, Stay Safe
The wrench attack economy thrives on public blockchain transparency. If crypto is going to replace traditional finance, it needs to stop doxxing its users by default.
Until then, your best defense is:
✔️ Use privacy coins where possible (XMR, ZEC, FIRO)
✔️ Obfuscate transactions (CoinJoins, Tornado Cash, PayNyms)
✔️ Never reuse wallet addresses
✔️ Keep small payments off-chain
✔️ Stop telling people you own crypto IRL
Remember: The best security is not being a target in the first place. 🚀