Supply Chain Attack
Supply Chain Attack Hits OPPO and Realme: Pre-loaded Loan Apps Spark Privacy Concerns
The recent controversy surrounding OPPO and Realme smartphones pre-loading unremovable loan applications highlights a concerning trend: supply chain attacks. While often associated with compromised software libraries affecting developers, this incident demonstrates how such attacks can manifest in the consumer electronics realm, raising serious questions about user privacy and manufacturer responsibility.
| 🧑🏾✈️ Serious Article: | This article is a serious piece and may deviate from the satirical nature of other content on this wiki. Please approach it with a serious mindset and consider its general applicability to topics such as banking, finance, personal safety, cybersecurity or even Brain functionality. |
|---|
The OPPO/Realme Incident: A Breakdown
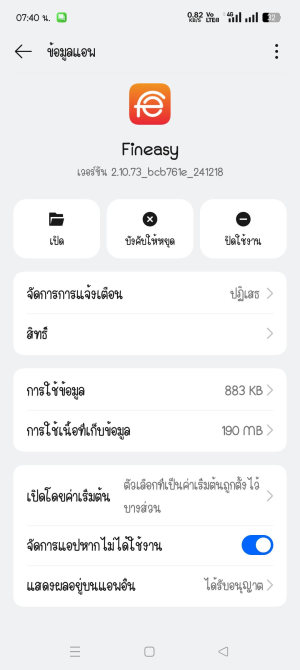
The Consumer Organization Council of Thailand (สภาองค์กรของผู้บริโภค) recently called out OPPO and Realme for pre-installing two financial applications, "สินเชื่อความสุข" (Sin Chuea Kwam Suk) and "Fineasy," on their devices without user consent. These apps, offering loan services, were reportedly difficult or impossible for users to uninstall, prompting widespread concern.
OPPO has since issued an apology and stated that the loan-related features have been removed from the Fineasy app, leaving only basic utility functions. They also promised to expedite a solution allowing users to uninstall Fineasy and pledged to halt pre-installation and promotion of all loan apps.
Supply Chain Attacks: A Broader Perspective
A supply chain attack occurs when a malicious actor compromises a part of the supply chain to distribute malware or unwanted software. In the software development world, this might involve injecting malicious code into a popular open-source library, which then infects all projects that use that library.
In the case of OPPO and Realme, the supply chain attack manifests differently. The operating system (ColorOS in OPPO's case) update process became the vector for distributing unwanted software. By pre-loading these loan apps during the manufacturing or OS update process, the manufacturers effectively bypassed user consent and installed software that users didn't explicitly choose.
Differences from Typical Software Supply Chain Attacks:
While the core principle is the same, there are key differences compared to a compromised npm (Node Package Manager) library scenario:
- Direct Distribution: In the OPPO/Realme case, the distribution vector is controlled directly by the device manufacturer, not a third-party code repository.
- Target Audience: The target is not developers but end-users of the devices.
- Motivation: While malicious npm packages often aim to steal data or inject further malware, the primary motivation in this case appears to be financial, potentially through revenue sharing or kickbacks from the app developers.
Implications and Concerns:
This incident raises several key concerns:
- User Consent and Control: Pre-installing unremovable apps violates user autonomy and control over their devices. It treats users as mere products to be monetized rather than valued customers.
- Privacy Violations: Financial apps often require access to sensitive user data. Installing such apps without consent raises serious privacy concerns, especially if the apps lack proper security measures or are not regulated by relevant authorities like the Bank of Thailand.
- Manufacturer Responsibility: The incident highlights the responsibility of device manufacturers to thoroughly vet the software they include in their products. They must ensure that users have control over their devices and that their privacy is protected.
- Potential Financial Incentives: The possibility of financial arrangements between app developers and manufacturers raises ethical questions and suggests a potential conflict of interest.
- PDPA Implications: Thai authorities, including the Digital Economy and Society Ministry (DE), are investigating whether this practice breaches the Personal Data Protection Act (PDPA).
The "Product" vs. "Customer" Mentality:
This situation underscores a disturbing trend where some companies view users as products to be monetized rather than valued customers. By pre-loading unwanted apps, manufacturers effectively turn their devices into advertising platforms, prioritizing profit over user experience and privacy.
Conclusion:
The OPPO/Realme incident serves as a stark reminder of the potential risks associated with supply chain attacks, even in the consumer electronics sector. It highlights the importance of user consent, manufacturer responsibility, and robust regulatory oversight to protect user privacy and prevent the exploitation of consumers. While the damage may not be as directly harmful as a malicious code injection into a software project, the breach of trust and the potential for privacy violations are significant. This case will likely lead to greater scrutiny of pre-installed apps and more pressure on manufacturers to prioritize user rights.